Import a CA certificate into MacOS
Import a CA certificate into the MacOS KeyChain Access application
Create the CA key and certificate
Open a terminal window.
Make sure you have the required command line tools installed by running python3. If you are asked to install the Command Line Developer Tools, please select .

Next, install pip in order to install the certificates manager scripts dependencies.
python3 -m ensurepip
Now, install the cryptography pip module to satisfy all the dependencies of the certificates manager scripts.
pip3 install cryptography
Once the installation completes, cd into the tools directory of your FairCom bundle.
cd <faircom>/tools/certman
Now, create the CA key files by running the following command:
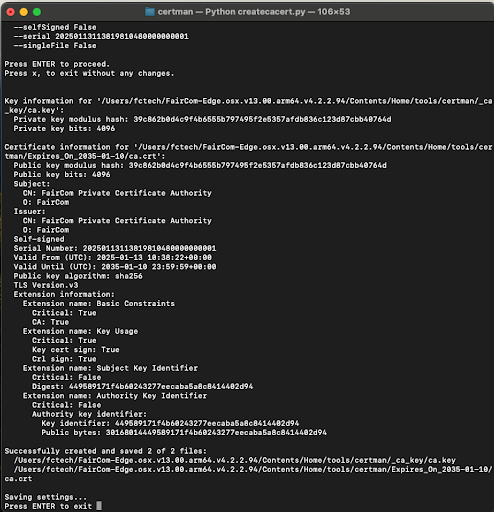
python3 createcacert.py
Make sure you enter all the requested parameters; otherwise, the script will not succeed. A successful run will show the following output:
Create a server certificate which is signed by the CA certificate being imported.
Make sure you are still in the
<faircom>/tools/certmandirectory with your terminal, then run:python3 createservercert.py
Make sure you enter the requested details for your server certificate before proceeding to the generation. Please also remember that if you add a passphrase to the certificate, you’ll need to enter the passphrase when you start up the server.
Configure the FairCom server to use the server certificate by editing the file
<faircom>/config/services.jsonand add the full path to the certificate you’ve generated in theserverCertificateNameproperty of the tls section under your https configured port. (8443 by default). Please refer to the code snippet below:"listeners": [ … { "serviceName": "https8443", "description": "Port 8443 using TLS-secured HTTPS protocol for REST and Web Apps on all TCP/IP addresses bound to this server", "port": 8443, "protocol": "https", "enabled": true, "tls": { "serverCertificateFilename": "/Users/fctech/FairCom-Edge.osx.v13.00.arm64.v4.2.2.94/Contents/Home/tools/certman/Expires_On_2026-02-12/FAIRCOMSServer.pem" } },Please note the path to
serverCertificateFilename.These optional steps do not need to be done prior to importing this certificate, but they will need to be done prior to testing the server certificate.
At this point, if you use your favorite browser to visit the FairCom Server homepage using the FQDN or the IP Address you used during the certificate creation process above, you will still get a security warning because the certification authority is not yet registered.
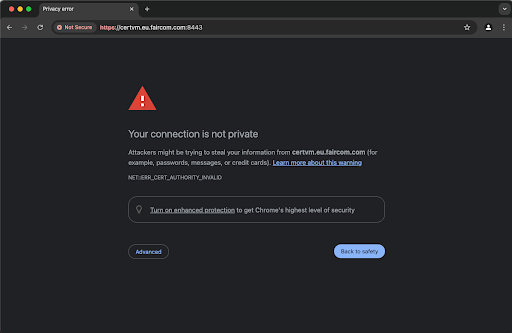
In the next section of this tutorial, we will show how to register the certification authority we've created above.
Use FairCom's certificate import utility
Open a terminal window.
In that window, navigate to FairCom's Certificate Management program at
<faircom>/tools/certman
Execute sudo python importcert.py
If you created a CA keypair using these tools, the program will detect those and ask you if you want to import that keypair. When you see a prompt like this Would you like to import the certificate at Certs\Expires_On_2034-08-12\ca.crt? Type in "yes" or "no".
If you respond "yes", you will be prompted to "Press ENTER to proceed".
If you respond "no", you will be prompted for the filename to import.
After having chosen the certificate to import you will be prompted with the interactive password enter to unlock the MacOS keychain and complete the import of the CA
If you now visit the FairCom Server https homepage using the FQDN or IP Address you’ve entered during the creation of the server certificate (See the Create a server certificate which is signed by the CA certificate being imported section above) you’ll see that the certificate in use is now trusted.
Execute the following command:
sudo security add-trusted-cert -d -r trustRoot -k /Library/Keychains/System.keychain certificate_filename
Note
We strongly suggest that you use this command from your MacOS terminal application. If you try to use this command via the remote login (SSH), you will not be able to import the certificate because the keychain can't be unlocked using the interactive prompt.
After the file has been imported, it can be verified using the KeyChain Access application of your MacOS system:
Open KeyChain Access.
Select from the left menu.
Now, on the right side of the KeyChain Access window, you should be able to see the FairCom private CA.
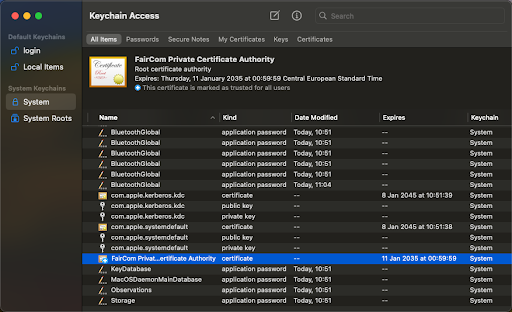
Double-click the FairCom Private Certificate Authority to see the certificate details with its trust level.

OpenSSL:
user@sonoma:~$ openssl verify -CAfile /etc/ssl/certs/ca-certificates.crt ca.crtca.crt: OK
Test the connection using Python
Python version 3.7 and later can access the OS trust store. This support may be library-dependent. To test with the "requests" library,
First, install the pip-system-certs package:
pip install pip-system-certs
Then test using these two lines of code (change
127.0.0.1to the address of your server):import request sprint( requests.Session().post( "https://127.0.0.1:8443/api", data = '{"api": "admin","action": "pingSession"}' ).json() )A successful run will show this output:
{'errorCode': 0, 'errorMessage': ''}