FairCom DB Notify
FairCom DB Notify and FairCom MQ non-secure and secure communications - tutorial
FairCom DB Notify allows you to define event criteria on any FairCom DB database file. The file is actively monitored and a FairCom DB Notify processing event is triggered when the criteria are satisfied. When triggered, FairCom DB Notify sends a configurable MQTT message to a specified MQTT Broker.
This tutorial describes how to set up these event criteria either with non-secure communication or with secure FairCom DB Notify communications between a FairCom DB Server and a FairCom MQ broker using Transport Layer Security (TLS) authentication.
Ensure that FairCom DB and FairCom MQ are installed and running.
Note
To run both products on the same computer, remap the ports used by one or both of the products. Change the SQL_PORT configuration setting in ctsrvr.cfg and the enabled ports in services.json. See: Run multiple server instances on one computer.
Configure FairCom DB Notify with or without TLS secure communications.
Enable the FairCom DB Notify Service for the FairCom DB server by editing the
<faircom>\config\services.jsonconfiguration file and changing the followingenabledsetting fromfalsetotrue."otherServices": [ { "serviceName": "dbnotify", "serviceLibrary": "./dbnotify/fcdbnotify.dll", "enabled": true },Edit the
<faircom>\config\dbnotifyconnections.jsonfile to configure a connection between your FairCom DB server and FairCom MQ. Set thefaircomServerNameto the name used by FairCom MQ. This defaults to"FCEDGEMQ". You can verify this by looking forSERVER_NAMEin the<faircom>/config/ctsrvr.cfgfile of your FairCom MQ server.Note
The
brokerHostnamespecifies the machine your FairCom MQ server is running on.{ "logLevel": "development", "directConnectionsToFairComMq": [ { "brokerConnectionName": "brokerCtree", "faircomServerName": "FCEDGEMQ", "brokerHostname": "localhost", "brokerUserName": "ADMIN", "brokerUserPassword": "ADMIN", "reconnectFrequencySeconds": 15, "metadata": {}, "defaultIncludePrimaryKey": "never", "defaultTagChanges": "never", } ] }Edit the
<faircom>\config\dbnotify\ctreeSQLcustmast.jsonfile to configure the DB notification criteria.When the DB Server enables the FairCom DB Notify service at startup, it looks in the
<faircom>\config\dbnotifyfolder for any.jsonfiles. Each.jsonfile is expected to contain the necessary information related to one table to be monitored. A separate.jsonfile is needed for each table you want to monitor.Set the
databaseNameto match the database that contains the table to be monitored. For this tutorial, it isctreeSQL.Set the
tableNameto match the table you want this file to apply to. In this tutorial, it iscustmast.Set the
ownerNametoadmin. This should match the user that created the table.Inside the
publishMqttMessagesarray add an entry for each type of MQTT message you want the FairCom DBserver to send to the FairCom MQ broker. Each entry can use one or more trigger types and include different fields and settings to create a specific type of MQTT message.Set the
topicto the MQTT topic you want this message type to notify on. For this tutorial, usetopic1.Set
brokerConnectionNameto the same name used above when defining the connection to FairCom MQ,brokerCtree.Set
triggersto an array of event types you want this message type to notify on.QoSis the quality of service FairCom MQ will use to publish the notification messages. This example uses QoS 0.recordFilteris an optional expression used to identify a subset of records to notify on. If left out it will notify on all records for the given triggers.includedFieldsis an optional array of field names to include in the notification. If left out all fields will be included.
{ "databaseName": "ctreeSQL", "tableName": "custmast", "ownerName": "admin", "publishMqttMessages": [ { "topic": "topic1", "brokerConnectionName": "brokerCtree", "triggers": [ "delete"], "QoS": 0, "recordFilter": "!stricmp(cm_custstat,\"CA\")", "includedFields": [ "cm_custnumb", "cm_custzipc", "cm_custcity" ], "includePrimaryKey": "never" }, { "topic": "topic1", "brokerConnectionName": "brokerCtree", "triggers": [ "insert", "update"], "QoS": 0, "recordFilter": "atoi(cm_custnumb) >= 1000", "includePrimaryKey": "never", "tagChanges": "forEachField" } ] }Restart the DB Server.
Notice
The server is now set up with DB Notify. You can proceed to Test DB notify and perform Troubleshooting if needed.
Complete these steps to secure TCP/IP communications between the FairCom DB Notify service and the FairCom MQ broker. This activates TLS for authenticating and encrypting the network communications.
Note
If the DB Notify service and the MQ broker are going to be run on the same computer, you must ensure that all ports for the DB Notify server are different from the ports used by the MQ server. See Configure ports and services
TLS support optionally allows database user authentication based on a client-provided certificate that is trusted by the server and is in the MQ broker's authorized user database. Users can be added using the ctadmn utility.
The terms TLS and Secure Socket Layer (SSL) are used synonymously throughout this document.
Create certificates
Set up FairCom MQ with TLS
Set up DB Notify on FairCom DB with TLS
When done, you will have files in the following locations:
File folder | FairCom DB running DB Notify | FairCom MQ running MQTT broker |
|---|---|---|
CA | No CA files are needed for ISAM because the CA certificate is included in the server key pair and all client key pairs. | No CA files are needed for ISAM because the CA certificate is included in the server key pair and all client key pairs. |
Server | The FairCom DB server key, server certificate with FairCom DB SAN, and CA certificates. | The FairCom MQ server key, server certificate with FairCom MQ SAN, and CA certificate. |
Client | The Client key, client cert, and CA cert. | No client files are needed. |
Note
You can use different server certs signed by the same CA, but as long as all the DNS names are listed in the SAN, you can use the same cert on both servers.
You can create certificates using the Python scripts provided in the <faircom>\tools\certman\ folder.
Note
Create certificates on the FairCom DB server so you only need to copy two files over to the MQ server.
For secure communications, you need to create a Certificate Authority (CA) certificate file and key file. These two files are a key pair. The CA certificate file is used when creating the server and client certificate files.
Note
FairCom recommends you create certificate files with the following general limits:
CA files expire after 120 months; name the files
ca.crtandca.keyServer certificate files expire after 48 months
The admin client certificate files expire after 24 months
Other client certificate files expire no later than 12 months
Certificates need to be recreated before existing certificates expire. The life of a certificate is determined by the --months argument. The "valid from" date will be the date on which the certificates were created, and the "valid until" date will be the --months value from that creation date.
Steps to create TLS certificates for secure communications using the FairCom-provided Python script files:
Open a command prompt or console.
Change to the
<faircom>\tools\certman\directory.Create the CA certificate and key files. Run
createcacert.pywith appropriate argument values:Note
Run
python createcacert.py --helpfor descriptions of the arguments.python createcacert.py --certManagementFolder Certs --outCertFile ca.crt --outKeyFile ca.key --months 120 --bits 2048 --commonName "Root CA" --org MyCompany --country US --state MyState --location MyCity --unit CompanyGroup
The output indicates where the files were saved.
Successfully created and saved 2 of 2 files: <faircom>/tools/certman/Certs/_ca_key/ca.key <faircom>/tools/certman/Certs/Expires_On_<future date>/ca.crt
Copy the
ca.crtfile into the current directory:copy <faircom>/tools/certman/Certs/Expires_On_<future date>/ca.crt .Note
The path may need to be in quotes if it has spaces in it.
Create a server certificate file for the FairCom DB server. Run
createservercert.pywith appropriate argument values:python createservercert.py --certManagementFolder Certs --outCertFile server.pem --singleFile True --months 48 --bits 2048 --cipher sha256 --commonName MyServer --altName localhost 127.0.0.1 ::1
--altNameshould include all hostnames and IP addresses you use when connecting to this server. This example shows three addresses, each separated by a space character.--commonNameis typically set to the hostname of the server.Some settings, such as
--org, are not included here because they were saved when the CA certificate was created, and future commands will use the saved settings.Append the CA certificate to the server certificate file:
type ca.crt >> server.pem
Create a client certificate for the admin user. Run
createclientcert.pywith the appropriate argument values:python createclientcert.py --certManagementFolder Certs --singleFile True --months 24 --bits 2048 --outCertFile admin_client.pem --commonName admin
--commonNamedesignates which FairCom account is associated with this client certificate.Append the CA certificate to the client certificate file:
type ca.crt >> admin_client.pem
Create a client certificate for each user. Run
createclientcert.pywith the appropriate argument values:python createclientcert.py --certManagementFolder Certs --outCertFile john_doe_client.pem --singleFile True --months 12 --bits 2048 --commonName JohnDoe
--commonNamedesignates which FairCom account is associated with this certificate.Append the CA certificate to the client certificate file:
type ca.crt >> john_doe_client.pem
To test your TCP/IP TLS connection, deactivate the Shared Memory Protocol even if you are connecting with TCP/IP internally. This is currently required for using TLS with client authentication. If the Shared Memory protocol is activated, the Shared Memory is automatically used when possible. Deactivate Shared Memory by commenting out its keyword in the
<faircom>\config\ctsrvr.cfgfile.; Communication protocols ; COMM_PROTOCOL FSHAREMM
Deny shared memory for SQL also by adding the following line:
SQL_OPTION NO_SHARED_MEMORY
Activate SSL in the FairCom MQ broker by uncommenting the SSL and x509 support in the
<faircom>\config\ctsrvr.cfgfile.;Here is where you can activate (un-comment)SSL SUBSYSTEM COMM_PROTOCOL SSL { ;This is the file name in your server's directory SERVER_CERTIFICATE_FILE server.pem ;For SSL you can specify (un-comment) a debug log file name DEBUG_LOG ssl.log ;Here you can restrict access to SSL ONLY. SSL_CONNECTIONS_ONLY YES ;Require clients to provide a x509 certificate VERIFY_CLIENT_CERTIFICATE YES ;Use x509 client certificate for database authentication x509_AUTHENTICATION YES ;Use the SUBJECT:CN from the client's certificate as their username x509_PATH CN ;SSL_CIPHERS AES256-SHA256:AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:AES256-GCM-SHA384 }Save your changes to
ctsrvr.cfg.If using Linux/Unix, or macOS, update
<faircom>\server\stopserverto stop the server when using TLS.#!/bin/sh echo Stopping the FairCom Database Engine... CTSSL_CLIENT_CERTIFICATE=admin_client.pem export CTSSL_CLIENT_CERTIFICATE CTSSL_CLIENT_KEY=admin_client.pem export CTSSL_CLIENT_KEY cd ../tools ./ctstop -AUTO none none "FCEDGEMQ@localhost^fssltcp"
Copy
server.pem,admin_client.pem, andjohn_doe_client.pemto the<faircom>\server\directory.
Run command-line utilities found in the <faircom>/tools/ folder to test that FairCom MQ is TLS-enabled with a TLS ISAM connection.
Restart FairCom MQ.
The log message
"Initialized SSL support."is written toCTSTATUS.FCS.Check that the server's configuration file (
ctsrvr.cfg) allows only SSL connections.SSL_CONNECTIONS_ONLY YESLaunch two different CMD shells and run these two commands in each of the CMD shells to set environment variables in both. These enable client certificate-based authentication.
set CTSSL_CLIENT_CERTIFICATE=admin_client.pem set CTSSL_CLIENT_KEY=admin_client.pem
(optional) Run the following to enable SSL-related diagnostic messages:
Set CTSSL_DEBUG_LOG=ssl.log
The CA certificate MUST be available to the client process as the file
ca.crtin the working directory. Copy the CA certificate to the file namedca.crtin the<faircom>\tools\folder.Copy <faircom>\tools\certman\Certs\Expires_On_<future date>\ca.crt <faircom>\tools\ca.crt
Verify that TLS connections are working correctly for the ctixmg, ctadmn, and ctixmb tools, and check each tool's connection type.
Verify connections
In the first CMD shell, from the FairCom MQ
<faircom>\tools\folder, run each of the following command lines one at a time to check each tool's connection type.These commands append
^fssltcpto the server name to request an SSL-enabled connection for an ISAM connection. In these examples, you may need to changeFCEDGEMQto match thectsrvr.cfgSERVER_NAME value of your MQ server.Be sure to use quotes on the command line.
It is not necessary to send user/password because the TLS certificate supplies the necessary credentials.
Note
NOTE: Some utilities have position-based arguments that must be supplied. When client certificate authentication is enabled, any supplied username or password is ignored.
ctixmg ADMIN ADMIN "FCEDGEMQ@localhost^fssltcp" ctadmn ADMIN ADMIN "" "FCEDGEMQ@localhost^fssltcp" ctixmg none none "FCEDGEMQ@localhost^fssltcp"
If you get an error such as "Could not initialize c-tree Plus" or "Could not logon to server", the configuration is not configured correctly. If you get a menu or are asked a question, the x509 connection is working.
Check the connection type
While one tool is running in the first CMD shell, run ctadmn in the second CMD shell from the FairCom MQ
toolsfolder whereca.crtis present.ctadmn none none "" "FCEDGEMQ@localhost^fssltcp" **** FairCom(R) Server Administration Utility **** 1. User Operations 2. Group Definitions 3. File Security 4. Monitor Clients Enter your choice (1-10), or 'q' to quit>> 4Enter 4 to choose
Monitor Clients.Monitor Clients: 1. List Attached Clients 2. Kill Client Enter your choice (1-2), or 'q' to return to previous menu>> 1Enter 1 to choose
List Attached Clients:Look at the
NodeNameof each client that is listed to find the ctixmg, ctadmn, or ctixmb tool you are currently running in the first CMD shell.You might have to press enter a few times because our tool might be last on the list after other internal MQ threads.
The following examples are outputs for the ctixmg and ctadmn tools, with the items of interest bolded.
UserID: ADMIN NodeName: ctixmg Task 20 Communications: FSSLTCP Memory: 235K Open Files: 3 Logon Time: 0:06 Tran Time: -- Rqst Time: 0:06 NoRequest Rqst# 196 OPNRFIL UserID: ADMIN NodeName: ctadmn Task 34 Communications: FSSLTCP Memory: 288K Open Files: 9 Logon Time: 7:38 Tran Time: -- Rqst Time: 7:38 NoRequest Rqst# 196 OPNRFIL
Communications: FSSLTCP, as in these examples, indicates the TCP/IP connection is using TLS.
Note: The following protocols are some of the more common TCP/IP connections you might observe:
F_TCPIP indicates an unencrypted ISAM TCP/IP connection. FSSLTCP indicates an SSL/TLS-enabled ISAM TCP/IP connection. SQL_TCPIP indicates an unencrypted SQL TCP/IP connection. SQL_SSLTCP indicates an SSL/TLS-enabled ISAM TCP/IP connection.
Enter q to return to the ctadmn main menu.
In the first command shell, kill the tool that is running by pressing ctrl-c,. Launch the next tool and check its connection type until all three tools are verified.
In the second CMD shell running the ctadmn tool, add the
JonDoeuser to your Server/Broker's database.User Operations: 1. Add New User 2. Remove Existing User 3. List Users Enter your choice (1-9), or 'q' to return to previous menu>> 1
Enter 1,
Add New User.Enter User Id >> Jon Doe Enter User Description >> Jon Doe
Answer the remaining prompts as you prefer. After the last prompt, press q to return to the main menu. Press q again to exit ctadmn.
Set two environment variables to establish the user
JonDoewith x509 authentication.set CTSSL_CLIENT_CERTIFICATE=john_doe_client.pem set CTSSL_CLIENT_KEY=john_doe_client.pem
Run the ctixmg tool again, without a user or password, to verify that the
JonDoeuser is correctly configured with a TLS connection. This should launch without a "Could not initialize c-tree Plus" error. You may need to changeFCEDGEMQto match yourSERVER_NAMEvalue.ctixmg none none "FCEDGEMQ@localhost^fssltcp"
With the FairCom DB installation, edit the
<faircom>\config\dbnotifyconnections.jsonfile to configure a secure connection between your FairCom DB server and the FairCom MQ Broker:Set the
faircomServerNametoFCEDGEMQ. This is theSERVER_NAMEof the MQ broker that is set in the/config/ctsrvr.cfgfile in the FairCom MQ installation.Enable
tlsandx509_authentication.At
tls, set thecertificateFilenamewith the name of the client-side certificate file that you previously created (server.pemin this tutorial).At
x509_authentication, setcertificateFilenamewith the FairCom ADMIN user certificate key you previously created (admin_client.pemin this tutorial).{ "logLevel":"development", "directConnectionsToFairComMq":[ { "brokerConnectionName":"brokerCtree", "faircomServerName":"FCEDGEMQ", "brokerHostname":"localhost", "reconnectFrequencySeconds":15, "tls":{ "certificateFilename":"server.pem", "enabled":true, "x509_authentication":{ "certificateFilename":"admin_client.pem", "enabled":true } } } ] }
Edit the
<faircom>\config\dbnotify\ctreeSQLcustmast.jsonfile to configure the DB notification criteria.When the DB Server enables the FairCom DB Notify service at startup, it looks in the
config\dbnotifyfolder for any.jsonfiles. Each.jsonfile is expected to contain the necessary information related to one database file to be monitored. A separate.jsonfile is needed for each database file you want to monitor.{ "databaseName":"ctreeSQL", "tableName":"custmast", "ownerName":"admin", "publishMqttMessages":[ { "topic": "topic1", "brokerConnectionName":"brokerCtree", "triggers":["delete"], "QoS":0, "recordFilter":"!stricmp(cm_custstat,\"CA\")", "includedFields":[ "cm_custnumb", "cm_custzipc", "cm_custcity" ], "includePrimaryKey":"never" }, { "topic": "topic1", "brokerConnectionName":"brokerCtree", "triggers":["insert","update"], "QoS":0, "recordFilter":"atoi(cm_custnumb) >= 1000", "includePrimaryKey":"never", "tagChanges":"forEachField" } ] }The
"topic": "topic1"on"brokerConnectionName":"brokerCtree"that you set up when you configured your connection is used for published messages.Note
You can optionally define the
"persistence table"for the topic in FairCom MQ that will receive the messages from DB notify by defining the following properties inctreeSQLcustmast.json:"persistenceDatabaseName":"replaceWithDatabaseName", "persistenceOwnerName":"replaceWithOwnerName", "persistenceTableName":"replaceWithTableName",If these properties are omitted, FairCom MQ will automatically define them.
Copy certificates to the
<faircom>\server\folder.FairCom DB Notify acts as a client of the FairCom MQ Broker, so we need to copy the client-side certificates to the FairCom DB server folder.
Copy the
server.pemfile (SSL client-side certificate) into your FairCom DBserverfolder.> copy .\<YourWorkFolder>\server.pem .\<faircom>\server\server.pem
Copy the
adminuser certificate file into the FairCom DBserverfolder (x509 authentication):> copy .\<YourWorkFolder>\admin_client.pem .\<faircom>\server\admin_client.pem
Switch to the machine that FairCom MQ is running on and use MQ Explorer to check if the topics are already there:
If you have already run FairCom DB Notify without x509 in this environment,
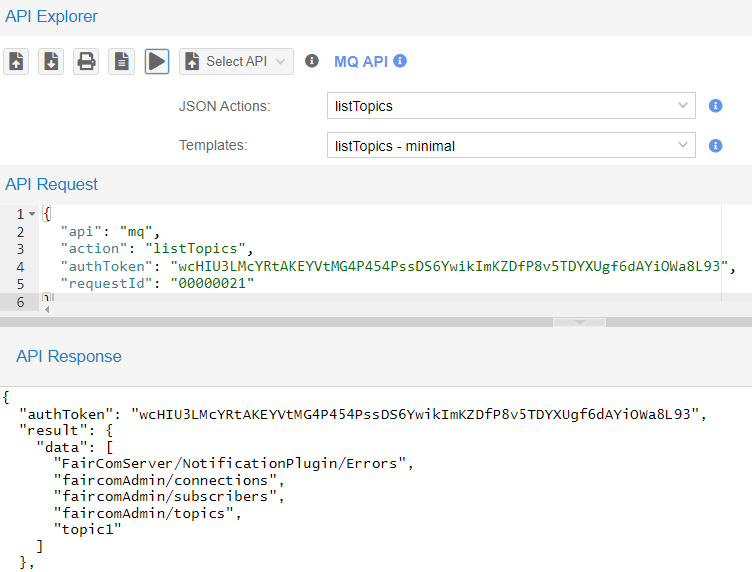
"topic1"and"FairComServer/NotificationPlugin/Errors"topics are already created and will appear in this list.In API Explorer, in the drop-down list choose MQ API.
In the drop-down list select listTopics then click Send request (
 ) to execute the
) to execute the listTopicsaction.The API Response will list all topics that are subscribed to in this broker.
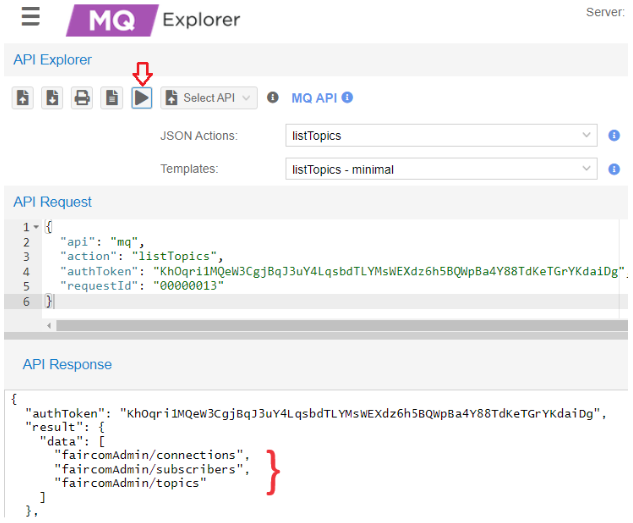
In this example,
"topic1"is not on the server.
Create topics
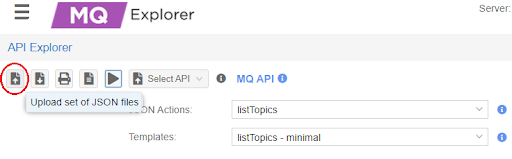
"topic1"and"FairComServer/NotificationPlugin/Errors"if they do not exist in the FairCom MQ broker.In API Explorer, click Upload Set of Json files (
 )
)
Select and upload
createErrorTopic.jsonandcreateTopic1.jsonfound in the<faircom>\config\x509.auth.demo\folder.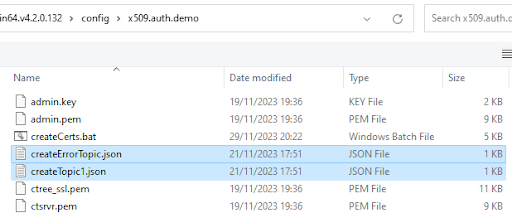
In select and execute the API request for each action.
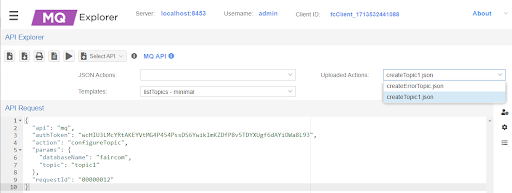
Execute listTopics again to show those topics.
Note: FairCom DB will support the automatic creation of topics with x509 in the future.
On the machine that FairCom DB is installed on, restart the FairCom DB Server.
Proceed to Test FairCom DB Notify using secure communication and x509 authentication.
How to set up non-secure or secure communications between FairCom DB Notify and FairCom MQ
At this point, both FairCom DB and FairCom MQ should be running. If you modified any config files in the previous steps, be sure to restart those servers so the changes take effect.
In FairCom DB, the <faircom> directory, create test files to use with DB Notify:
There are two SQL scripts to assist with this tutorial. The
custmast1.sqlscript creates files to monitor, andcustmast2.sqlmodifies the files. Copy both of the script files to your.\toolsdirectory.copy config\x509.auth.demo\custmast1.sql .\tools copy config\x509.auth.demo\custmast2.sql .\tools
Run the following command from the
.\toolsdirectory to createcustmast.isql -s custmast1.sql -u ADMIN -a ADMIN ctreeSQL INIT DEFINE Create table... MANAGE Add records... 1 record inserted. 1 record inserted. 1 record inserted. 1 record inserted. Display records... NUMBER NAME ------ ---- 1000 Bryan Williams 1001 Michael Jordan 1002 Joshua Brown 1003 Keyon Dooling 4 records selected DONE
The resulting files are saved in
<faircom>\data\ctreeSQL.dbsadmin_custmast.datadmin_custmast.idx
In MQ Explorer, on the FairCom MQ machine Subscribe to
topic1.Leave the "MQTT Management" window open to view "Incoming Messages - streaming".
On the FairCom DB machine, initiate some FairCom DB Notify activity in FairCom DB.
From
<faircom>/tools, execute the following command:isql -s custmast2.sql -u ADMIN -a ADMIN ctreeSQL
This runs a script that performs an update, a delete, and an insert command for the
custmastfile that triggers notification messages.In MQ Explorer, on the FairCom MQ machine, view the messages in MQ Explorer - MQTT Management.
(Run
custmast2.sqlmultiple times to see more incoming notifications.)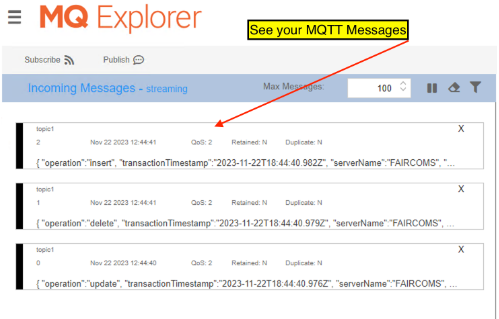
SSL problems
If you have trouble solving errors, you can enable a debug log on both the server-side and client-side.
One of the keywords you uncommented in step 2 in the Broker
ctsrvr.cfgfile was DEBUG_LOG ssl.logYou can review the server-side
ssl.log(typically located in the directory where faircom.exe is executed from) for server-side details.You can also enable client-side debugging by setting the following environment variable:
set CTSSL_DEBUG_LOG=ssl_client.log
Where
ssl_client.logis an arbitrary file name. Look for this file to be created where you are executing your client application.Could not initialize c-tree Plus(R) (1104)
Check if
server.pemwas copied into your Apps folder andctree_ssl.pemto the/server/folder.This can be a problem during configuration. For example, FairCom MQ requires a secure connection (SSL) and the client is not using SSL.
X509 environment variables were not set while running a command line program.
NOTE: Enabling SSL client-side debugging may help to figure out the problem. Also, check
ssl.login the data folder.Could not logon to server 'FCEDGEMQ@localhost^fssltcp'. Error #162.
The server has broken its connection with the application.
Typically this is because you either do not have your user certificate (
admin.pem) or key (admin.key) files in place or you have not set your environment variables.Executing isql with ssl.
SQL doesn't support x509 authentication yet.
error(-30033): No data
Executing isql with ssl..
SQL doesn't support x509 authentication yet.
error(-30034): Network error on server
Executing isql with ssl..
SQL doesn't support x509 authentication yet.
error(-18104): CT - SSL connection attempt failed
You are executing a client with SSL, trying to connect to a server without SSL or vice-versa.
Could not initialize c-tree Plus(R) (128)
Verify if variables
CTSSL_CLIENT_CERTIFICATEandCTSSL_CLIENT_KEYwere set and exported (linux).error in tcp bind 10060 error(-20212): Error in Network Daemon Could not logon to server 'FCEDGEMQ@localhost^fssltcp'. Error #133. Server is not operational. The server is not running.
At
CTSTATUS.FCS, there are messages like:CheckTopics error. Not possible to open table [admin_mqtt_msg_topic1].: 4023 CheckTopics error. Not possible to open error table [admin_mqtt_msg_faircomserver_notificationplugin_errors].: 4023
It is necessary to create topics
topic1andFairComServer/NotificationPlugin/Errorsat FairCom MQ. See Set up DB Notify with SSL and x509.DB Notify errors
To fix connection errors or ensure that table configurations were set successfully, set the
logLeveltodevelopmentatdbnotifyconnections.json.This causes DB Notify to show status messages at
CTSTATUS.FCS. See Configure connnection.{ "logLevel": "development", "directConnectionsToFairComMq": [ { "brokerConnectionName": "brokerCtree", "faircomServerName": "FCEDGEMQ", "brokerHostname": "localhost", "tls": { "certificateFilename": "server.pem", "enabled": true, "x509_authentication": { "certificateFilename": "admin.pem", "privateKeyFilename": "admin.key", "enabled": true } } } ] }