Secure MQTT with certificates
Tutorial to configure FairCom servers to use secure MQTT connections with CA, server, and client certificates
This tutorial shows how to use CA, server, and client certificates to secure MQTT communications in FairCom Edge and FairCom MQ servers. Certificates are more secure than a username and password.
Prerequisites
Download, install, and start up FairCom MQ or FairCom Edge.
Identify the <faircom> folder where you installed the FairCom product. Some steps in this tutorial use this folder.
The certificate management scripts in this tutorial use Python. Follow these setup instructions to ensure that Python is installed and configured correctly.
On the computer where you installed the FairCom server, launch a Windows CMD prompt or Linux command line shell, change to the<faircom>/tools folder, and run the following command:
FairCom MQ
sa_admin -aADMIN -pADMIN -f"" -sFCEDGEMQ -oua user1 -w pass1FairCom Edge
sa_admin -aADMIN -pADMIN -f"" -sFAIRCOMS -oua user1 -w pass1
This command adds the user1 account to the server for subsequent use in this tutorial. If you want to add additional usernames, run the command again with new values for user1 and pass1. You do not need to add the admin account to the server because it is built-in.
This tutorial uses the FairCom Certificate Manager to create certificates. Once you create your own private certificate authority (CA) files, you can use them to create server and client certificates.
Launch a Windows CMD prompt or Linux command line shell, change to the
<faircom>/tools/certmanfolder.Run the
createcacert.pyscript and answer the prompts. For help, see the Easy section in the documentation.When prompted for your
company name, enter your company's official name and press ENTER.When prompted for a
directoryto manage certificates, enter a folder name likeC:\certsand press ENTER.When prompted for
years, press ENTER to expire the CA certificate in10years.Press ENTER to create the CA certificate files.
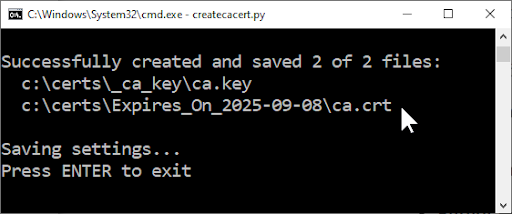
Copy the
ca.crtfile just created into the<faircom>/serverfolder.Copy the
ca.crtfile into a certificate folder used by your client software. This Python MQTT tutorial is an example of client software using TLS and client certificates.Optionally use this OS Keystore tutorial to install the
ca.crtfile in each computer where you use the Google Chrome browser to run FairCom's browser-based applications.
A server certificate securely identifies your FairCom server to clients. It protects your MQTT clients from man-in-the-middle attacks.
Before starting, gather the server's hostname, DNS names, and IP addresses.
Use the command line shell you previously opened to the
<faircom>/tools/certmanfolder.Run
createservercert.pyand answer the prompts. For help see the Easy section in the documentation.When prompted for the
server hostname, you must enter the server's DNS name and press ENTER.To determine the server's hostname, open a command prompt on the target server and use the command
hostnameto display the server's hostname.This application uses the
hostnameas the first part of the certificate filename followed byServer.pem. It also adds it to the certificate in the Subject Common Name (CN).In this example, the
hostnameisapolloand the server certificate filename isapolloServer.pem.
When prompted for
months, press ENTER to expire the certificate in13months or enter another value.When prompted for the server's
IP Addresses and DNS names, you must enter an IP Address or a DNS name and press ENTER.This information is required and must be correct or clients will reject the server certificate. If clients connect to the server using a hostname, you must include it in the certificate. Likewise, if clients connect to the server using an IP Address, you must include it in the certificate.
Each value you enter is stored in the certificate extension called Subject Alternative Name (SAN).
If the server is your local computer, you should enter
127.0.0.1andlocalhostso clients can connect using either one.You will be repeatedly prompted to enter another IP Address or DNS name.
Press ENTER to exit the prompt for more
IP addresses and DNS names.
When prompted for a
country code, optionally enter the two-character abbreviation of your country, such asUS, and press ENTER.When prompted for a
state, optionally enter the abbreviation of your state, such asUT, and press ENTER.When prompted for a
city, optionally enter the name of your city, such asSalt Lake City, and press ENTER.When prompted for a
department, optionally enter the department that manages certificates, such asIT Security, and press ENTER.When prompted for an
email, you must enter the email address of your security administrator and press ENTER.Press ENTER to create the server certificate.
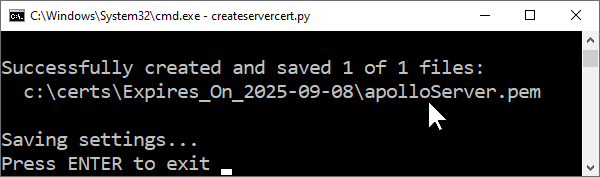
Copy the
pemfile just created into the<faircom>/serverfolder.
You need to create two client certificates: one for the user1 account you created earlier and another for the built-in admin account. To do so, you will run createclientcert.py twice with different information each time.
Use the command line shell you previously opened to the
<faircom>/tools/certmanfolder.Run
createclientcert.pyand answer the prompts. For help see the Easy section in the documentation.When prompted for the
Common Name, enteruser1, which is the username of an account, and press ENTER.When prompted for the certificate passphrase, press ENTER to omit it.
When prompted for
months, press ENTER to expire the certificate in13months.When prompted for a filename containing
IP addresses and DNS names, press ENTER twice to omit it.Press ENTER to create the client certificate.
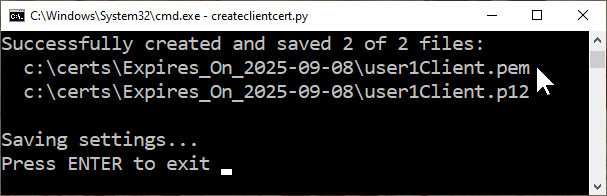
Again run
createclientcert.pyand answer the prompts.When prompted for the
Common Name, enteradmin, which is the username of the built-in admin account.When prompted for the certificate
passphrase, press ENTER to omit it.When prompted for
months, press ENTER to expire the certificate in13months.When prompted for a filename containing
IP addresses and DNS names, press ENTER twice to omit it.Press ENTER to create the client certificate.
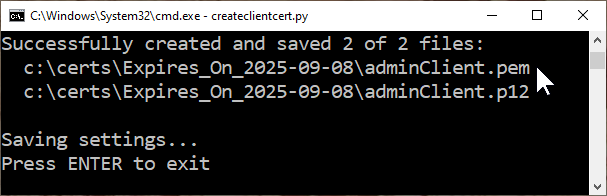
Copy the
user1Client.pemfile to the computer running your MQTT client software.Copy the
adminClient.pemfile to the<faircom>/serverfolder.This file secures internal MQTT connections inside the FairCom server.
You need to change two configuration files and restart the server to enable certificates and secure the server.
Update ctsrvr.cfg
Modify the the <faircom>/config/ctsrvr.cfg file as follows.
Add a semicolon
;to the beginning of the line containingCOMM_PROTOCOL FSHAREMMto turn off the shared memory protocol.Remove the semicolon
;from the beginning of the line containingSUBSYSTEM COMM_PROTOCOL SSL {to enable secure communications over TLS (SSL).Remove the semicolon
;from the beginning of the line containingSERVER_CERTIFICATE_FILE ctree_ssl.pemto enable the server certificate.Remove the semicolon
;from the beginning of the line containingx509_AUTHENTICATION YESto enable client certificates.Remove the semicolon
;from the beginning of the line containingx509_PATH CNto tell the server to use the Common Name (CN) for the username's location in the client certificate.Change the server certificate filename from
ctree_ssl.pemto the filename of the server certificate you created. It is the hostname of your server plusServer.pem, such asapolloServer.pem.Save your changes to
ctsrvr.cfg.
Update services.json
Modify the <faircom>/config/services.json file as follows.
Set the
"enabled"property tofalsefor the"http8080","mqtt1883", and"mqttws9001"protocols in the"listeners"list. This step disables these insecure protocols.Do the following In the
"tls"property of each secure listener:"https8443","mqtts8883", and"mqttwss9002".Set
"certificateFilename"to the name of the server certificate file, such as"apolloServer.pem".
Do the following in the
"tls"property of the listener:"mqtts8883".Set
"certificateAuthoritiesFilename"toca.crt, which is the name of the CA certificate file.Set the
"clientCertificateFilename"to"adminClient.pem", which is the name of the admin client certificate file.
In the
"mqtt"object, change the"authenticationMethods"property to"authenticationMethods": [ "clientCertificate" ]to restrict MQTT authentication only to client certificates.Save your changes to
services.json.Verify your changes are similar to the following excerpt from the
services.jsonfile. Do not replace theservices.jsonfile with the following.{ "listeners": [ { "serviceName": "http8080", "port": 8080, "protocol": "http", "enabled": false }, { "serviceName": "https8443", "port": 8443, "protocol": "https", "enabled": true, "tls": { "certificateFilename": "apolloServer.pem" } }, { "serviceName": "mqtt1883", "port": 1883, "protocol": "mqtt", "enabled": false }, { "serviceName": "mqtts8883", "port": 8883, "protocol": "mqtts", "enabled": true, "tls": { "certificateFilename": "apolloServer.pem", "certificateAuthoritiesFilename": "ca.crt", "clientCertificateFilename": "adminClient.pem" } }, { "serviceName": "mqttws9001", "port": 9001, "protocol": "mqttws", "enabled": false }, { "serviceName": "mqttwss9002", "port": 9002, "protocol": "mqttwss", "enabled": true, "tls": { "certificateFilename": "apolloServer.pem" } } ], "mqtt": { "authenticationMethods": [ "clientCertificate" ] } }Restart the FairCom server to apply the changes.
A client application must connect to MQTT port 8883 to create a secure TLS connection with the broker. Connecting to MQTT port 1883 creates an insecure connection.
The following tutorials show how to use a client certificate to connect clients securely to MQTT:
Python MQTT tutorial - use Python to connect securely to MQTT.
Java MQTT tutorial - use Java to connect securely to MQTT.
Node-RED MQTT tutorial - use Node-RED to connect securely to MQTT.